Mark Sunner, Chief Security Analyst at MessageLabs was among the many security analysts watching one Trojan called “Spam Thru”, a piece of malware designed to send spam from an infected computer, at the turn of last year. Spam Thru represented an expontential jump in the level of sophistication and complexity of these botnets, harnessing a 70,000 strong peer to peer botnet seeded with the Spam Thru Trojan. Spam Thru is also known by the Aliases Backdoor.Win32.Agent.uu, Spam-DComServ and Troj_Agent.Bor.
Spam Thru was unique because it had its own antivirus engine designed to remove any other malicious programs residing in the same infected host machine so that it can get unlimited access to the machine’s processing power as well as bandwidth. It also had the potential to be 10 times more productive than most other botnets while evading detection because of in-built defences.
The thing that worries Mark Sunner the most is that he suspects the major traffic spike towards the end of 2006 was merely a test run for more if not similarly sophisticated botnets to follow. Sunner adds
” With new levels of sophistication this has reached a real milestone. Botnets are getting smaller, more stealthy and more discreet and yet the volumes of spam are going up. Without a hint of scaremongering, will this get a lot worse throughout 2007 in terms of botnet sending? Absolutely, yes.”
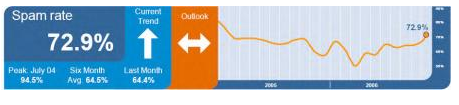
The British IT-Sicherheitsfirma Message Lab registered a dramatic increase in Spam Mail traffic from 64.4% to 72.9% late last year, all attributed to Spam Thru.
How does Spam Thru work?
The Spam Thru Trojan uses peer-to-peer technology to send commands to hijacked computer. The concept of viruses and Trojans attempting to block anti-virus software on the host machine they are trying to infect is nothing new. They do this by tweaking hosts file to the anti-virus update sites, killing processes, removing registry keys etc. SpamThru does this by downloading a cracked copy of Kaspersky AntiVirus and scans the host machine for malware setting them up for deletion at the next reboot while skipping over files it detects are part of its own installation.
According to the research done by Joe Stewart, a senior security researcher, SpamThru takes the game to a whole new level, actually using an anti-virus engine against potential rivals. He adds
” It is simply to keep all the system resources for themselves—if they have to compete with, say, a mass-mailer virus, it really puts a damper on how much spam they can send”
SpamThru creates the following registry entries:
HKCR\CLSID\(2C1CD3D7-86AC-4068-93BC-A02304BB8C34)\InProcServer32
<default>
<Path to Trojan DLL>HKCR\CLSID\(2C1CD3D7-86AC-4068-93BC-A02304BB8C34)\InProcServer32
ThreadingModel
ApartmentHKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ SharedTaskScheduler
(2C1CD3D7-86AC-4068-93BC-A02304BB8C34)
DCOM ServerHKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\ ShellServiceObjectDelayLoad
DCOM Server
(2C1CD3D7-86AC-4068-93BC-A02304BB8C34)
SpamThru is being used to send out mails such as the one below besides pump-and-dump stock schemes.
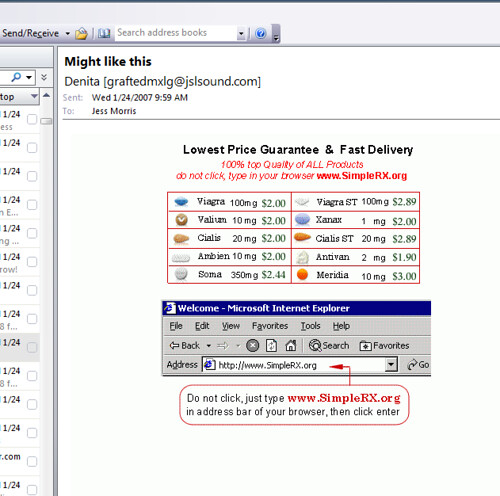
or something like this
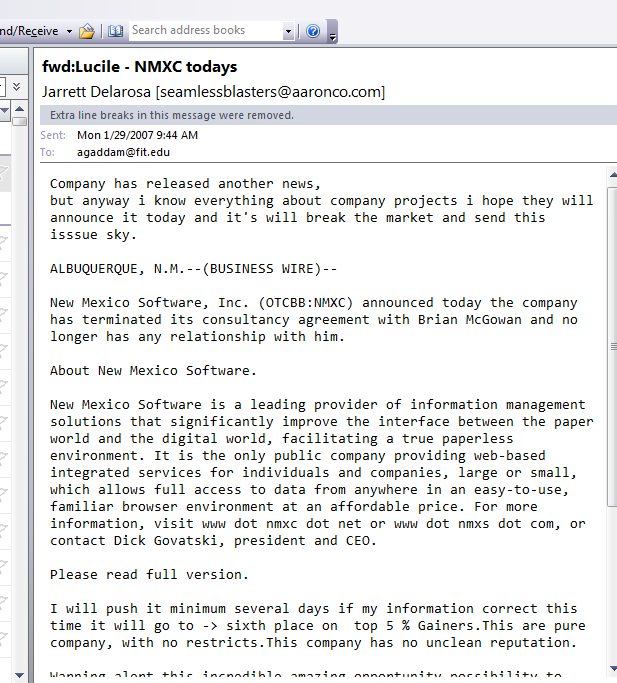
Some of the advances made by SpamThru on the level of compexity of Trojans
1. Highly efficient usage of P2P technology. In case the control server is disabled, the spammer can updated his botnet with the location of a new control server as long as he maintains control over atleast one peer.
2. The SpamThru Trojan randomizes the GIF files changing the width and height of the spam messages it is sending out, so as to defeat the anti-spam solutions that reject e-mail based on a static image.
References:
EWeek article on SpamThru: Spam Trojan Installs Own Anti-Virus Scanner