Google Chrome holds a market share of about 25% of the overall web browser market. It is growing faster and gaining more market share by the day than all the browsers out there. Most of these users seek to extend their usage of the Google Chrome browser to their work environment. The reason Internet Explorer is the dominant browser used in most companies is because Microsoft makes it easy to centrally deploy, manage, upgrade, and configure their web browser across a large number of Windows systems in the enterprise.
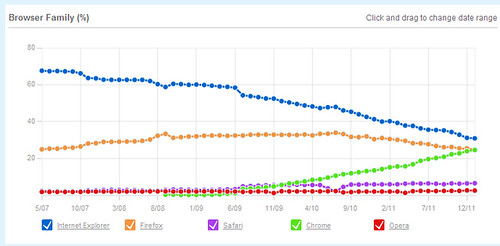
Figure 1: Global Browser Trend Data as of December 2011 from W3Counter.com
Google understands this and released Google Chrome for Business that enables an Enterprise IT department to easily configure and deploy Google Chrome on Windows, Mac, and Linux environments.
From an Information Security perspective, Google Chrome has been shown as the most secure browser with security features like Sandboxing, JIT hardening, ASLR, and DEP protection. You can read the full Accuvant Labs report here (pdf). http://www.accuvant.com/sites/default/files/AccuvantBrowserSecCompar_FINAL.pdf
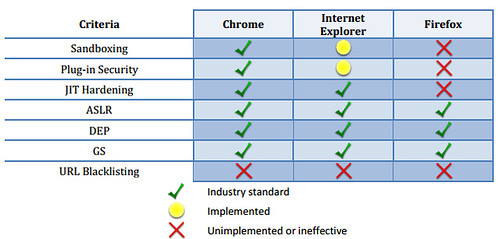
In order to set Google Chrome Security Settings for the Business edition, you need to download couple items first from Google. They include the Google Chrome MSI and the ADM files which we will use to set Security settings for Google Chrome.
Google Chrome MSI and ADM files
Google Chrome for Business is available as an MSI installer package. What this means is that it allows enterprises to centrally roll out and update the browser using Group Policy or any other standard deployment tools to all their managed users.
Step 1: Download the Google Chrome MSI
https://www.google.com/intl/en/chrome/business/browser/
Step 2: Download the Google Chrome policy templates
The next step is to securely configure Google Chrome. Google provides policy templates, an ADM and an ADMX template. There are templates available for Linux with JSON files and Mac with MCX configuration as well.
Zip file of Google Chrome templates and documentation: http://dl.google.com/dl/edgedl/chrome/policy/policy_templates.zip
Step 3: Configure using Group Policy Editor
- Launch Group Policy Editor Start > Run > gpedit.msc
- Import the Google Chrome ADM template
- Right click on Administrative Templates under Local Computer Policy > Computer Configuration > Administrative Templates
- Under Add/Remove Templates, add the chrome.adm file (for Windows in the zip file, it is under Policy Templates > Windows > adm > en-US
- Once complete, a Google folder will appear under Administrative Templates
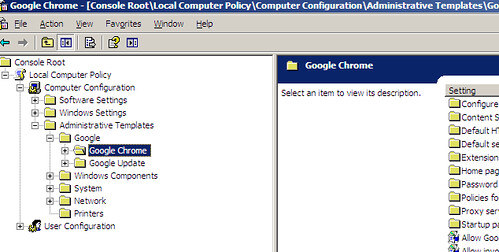
Figure 3: Google Chrome ADM template in Group Policy Editor
Google Chrome Security Settings Configuration
The following sections are recommendations for securely configuring Google Chrome for your enterprise. Please make sure to test the recommended configurations and tweak them as appropriate.
Google Update for Enterprise
This enables your enterprise to customize policies for Google update. The recommendation is to enable the Auto-update function in Google Chrome. If this option is not acceptable to your IT department for testing, reporting, or other management reasons, the Auto Update functionality can be disabled and you can follow the normal patch management/deployment cycle.
Now this route probably runs contrary to how you deploy software and OS patches at your company. The reasons are valid where you want to test for patches, assess and prioritize the risk, and roll them out in some fashion. What you may want to keep in mind is that the web browser represents the single greatest threat vector to companies and it may be prudent to update the browser as soon as possible. With that said, the template used: http://dl.google.com/update2/enterprise/GoogleUpdate.adm
Current Settings (Google -> Google Update -> Google Chrome):
- Enable the Allow installation option to install Google Chrome updates including security updates using Google Update/Google Installer.
- Under “update policy override,” select the Automatic silent updates option where updates are automatically applied when they are found via the periodic update check.
- Check for auto updates once every 24 hours or 1440 minutes. Under Preferences, enable the Auto-update check period override and set it to a value of 1440.
- Configure the Proxy Server settings. The recommendation is to customize via a .pac proxy script.
Configure Remote Access Options
This option enables remote clients to discover and connect to the user’s machine even if they are separated by a firewall.
- Disable the “Enable firewall traversal from remote access host” option.
Content Settings
This section customizes the JavaScript and other content rendering within the Chrome browser.
- JavaScript is set to power the future of the web. Leave it to a “not configured” state and let the user choose when they want to deny a particular website from executing JavaScript.
- Disable the Default Plugins setting. Customize plugin functionality through an approved whitelist by using the Allow plugins on these sites.
- Leave the Default popups setting to “not configured.” This option will enforce the BlockPopups behavior by default and the user will be able to change it.
- Enable the Default Geolocation setting and choose the “Ask whenever a site wants to track the user” option.
Google Chrome Frame
Google Chrome frame is not recommended as a secure alternative to render HTML in legacy browsers at this point.
- Disable the default HTML renderer for Google Chrome Frame
- Disable the Always render the following URL patterns in Google Chrome Frame
- Disable the Always render the following URL patterns in the host browser
Default Search
This setting controls the default search provider to be used when a user types text in the omnibox that is not a URL.
- There is no recommendation from Security for a default search provider. We recommend leaving it to the user to choose a provider of their choice.
Extensions
This option lets us customize the extensions the user can or cannot install. Make sure that all the extensions if any are approved and have a valid business case at your company. Disable this functionality and whitelist the approved extensions when required.
- Enable the Configure extension installation blacklist and choose a value of ‘*’ to blacklist all extensions.
- Disable the Configure extension installation whitelist unless there are approved exceptions.
Homepage
There is no recommendation for the default homepage. Users should be given the flexibility to configure it to a homepage of their preference.
Password Manager
Using the default password manager built into Google Chrome is not recommended as a viable password storage mechanism at this point.
- Disable the Enable the password manager option to prevent the saving of passwords or using already saved passwords.
- Disable the Allow users to show passwords in Password Manager. This prevents the password manager from not showing passwords in clear text in the password manager window.
HTTP Authentication
HTTP supports authentication using the WWW-Authenticate request headers and the Authorization response headers.
- Disable the basic access authentication method, which transmits credentials in plaintext to the server or proxy.
- Configure the authentication schemes to “digest, ntlm, negotiate.” The default Chrome behavior chooses Negotiate first followed by NTLM and finally the digest mode.
- Choose the CNAME lookup option to “not configured” for determining the canonical name of the server via CNAME lookup instead of using the server name.
- Choose the authentication server whitelist to “not configured.” With this option, the servers in the Local Machine or Local Intranet security zone are in the permitted list.
- Disable the Cross-origin HTTP Basic Auth prompts option. This controls whether third-party sub-content on a page is allowed to pop-up an HTTP basic authentication dialog box. This is disabled as a phishing defense. If a challenge comes from a server outside of the permitted list, the user will need to enter the username and password.
Proxy Server
This section enables us to specify the proxy server used by Google Chrome. Configure it to your current proxy settings. If you are using IE, you can easily replicate those current settings.
Chrome Detailed Security Configuration Settings
|
Configuration |
Setting |
Rationale |
| Allow Google Chrome Frame to handle the listed content types |
Disabled |
Google Chrome frame is not being presented as a secure option |
| Allow invocation of file selection dialogs |
Not configured |
Allow file selection dialogs as normal |
| Allow running plugins that are outdated |
Disabled |
Outdated plugins are prevented from running as normal plugins |
| Enable alternate error pages |
Not configured |
Enables the use of alternate error pages built into Google Chrome |
| Always run plugins that require authentication |
Disabled |
External plugins are disabled unless whitelisted via approved business case |
| Application locale |
Not configured |
Defaults to en-US and lets users customize |
| Enable AutoFill |
Disabled |
Prevents auto completion of forms using previously stored information such as credit card numbers |
| Block third party cookies |
Not configured |
User discretion |
| Enable bookmark bar |
Not configured |
User discretion |
| Clear site data on browser shutdown |
Not configured |
Preserves site data on browser shut down and user will be able to change it |
| Enable Google Cloud Print Proxy |
Disabled |
Prevents the local computer from acting as a proxy to share its local printers with Google Cloud Print |
| Enable submission of documents to Google Cloud Print |
Disabled |
Prevents users from submitting print jobs to Google Cloud Print |
| Set Chrome as Default browser |
Not configured |
User discretion |
| Disable Developer Tools |
Not configured |
Allows access to developer tools and the JS console |
| Disable support for 3D graphics APIs |
Not configured |
User discretion |
| Specify whether the plugin finder should be disabled |
Disabled |
Prevents search for and installation of non-approved plugins |
| Disable SPDY protocol |
Not configured |
Allows usage of SPDY protocol |
| Specify a list of disabled plugins |
Not configured |
Setting customized by EnabledPlugins and DisabledPluginsExceptions |
| Specify a list of plugins that the user can enable or disable |
Not configured |
Setting customized by EnabledPlugins and DisabledPluginsExceptions |
| Disable URL protocol schemes |
Not configured |
All listed protocol schemes are set to be accessible in Chrome |
| Set disk cache directory |
Not configured |
User discretion |
| Set disk cache size in megabytes |
Not configured |
User discretion |
| Enable network prediction |
Not configured |
User discretion |
| Set download directory |
Not configured |
User discretion |
| Enables or disables bookmark editing |
Not configured |
User discretion |
| Specify a list of enabled plugins |
Disabled |
Prevents installation of non-approved plugins |
| Enterprise web store name |
Not configured |
Customize to your internal App Store |
| Enterprise web store URL |
Not configured |
Customize to your internal App Store |
| Set Google Chrome Frame user data directory |
Disabled |
Chrome Frame is disabled |
| Prevent app promotions from appearing on the new tab page |
Enabled |
Promotions for Chrome Web Store apps will not appear on the new tab page |
| Import bookmarks from default browser on first run |
Not configured |
User discretion |
| Import browsing history from default browser on first run |
Not configured |
User discretion |
| Import of homepage from default browser on first run |
Not configured |
User discretion |
| Import saved passwords from default browser on first run |
Disabled |
Prevents import of saved passwords from current IE browser |
| Import search engines from default browser on first run |
Not configured |
User discretion |
| Incognito mode availability |
Disabled |
Set to Incognito Mode disabled. This data aids in investigations and forensic analysis if required |
| Enable instant |
Not configured |
User discretion |
| Maximal number of concurrent connections to the proxy server |
Not configured |
The default value of 32 will be used to specify the max number of simultaneous connections to the proxy |
| Set media disk cache size |
Not configured |
User discretion |
| Enable reporting of usage and crash-related data |
Disabled |
Prevents reporting of usage and browser crash related data to Google |
| Enable printing |
Not configured |
User discretion |
| Enable safe browsing |
Enabled |
Enables the safe browsing feature including phishing and malware protection |
| Disable saving browser history |
Disabled |
Saves browsing history |
| Enable search suggestions |
Not configured |
User discretion |
| Show Home button on toolbar |
Not configured |
User discretion |
| Disable synchronization of data with Google |
Enabled |
Prevent synchronization of data, for example with Google Docs |
| Enable Translate |
Not configured |
User discretion |
| Block access to a list of URLs |
Not configured |
Managed via Proxy |
| Allows access to a list of URLs |
Not configured |
Managed via Proxy |
| Set user data directory |
Not configured |
User discretion |
References
http://googleenterprise.blogspot.com/2010/12/chrome-is-ready-for-business.html
http://dev.chromium.org/administrators/policy-list-3
http://support.google.com/installer/bin/answer.py?hl=en&answer=146164
https://support.google.com/chrome/bin/answer.py?hl=en&answer=95589&topic=14666&ctx=topic
http://dev.chromium.org/developers/design-documents/http-authentication
http://support.google.com/installer/bin/answer.py?hl=en&safe=active&answer=146164
Excellent guide. Thank you. I have been trying hard to present a business case for Google Chrome at my company
do you have something for IE8?
Google Chrome
http://pdtechguru.wordpress.com/2012/09/25/google-chrome-group-policy
Can you tell how we can manage it centrally by admin user and how sub users can created and admin can manage it?
I’m looking for the setting that clears site data on browser shutdown but I can’t find it in the policy, could you tell me where to find this? Thank you
Thanks for the guide.
Looking at the Administrative Template > Computer Configuration & User Configuration that comes with the chrome.admx, they have the same settings.
Does this mean we choose to use either Machine OR User policies.
I.E, some GPO, for example Office they comes in pairs (need to have both Machine & Computer policies). Wondering if this the same case for Google Chrome where if Machine policies does not exist, then the User policies will not be processed … etc?
thank you
Great post my friend, just what I was looking for.
This post just saved my day 🙂 Thanks guys!
To turn out to be an professional in poker, it is not possible to do it within 1 day. Those are only a few factors, and as you can see some are healthy and some aren’t. What if you want to do magic methods with your playing cards?