The Federal Bureau of Investigation (FBI) has issued a code cracking challenge today. This was in response to a similar challenge the FBI issued last year, which proved to be hugely popular with many thousands responding to the crypto challenge.
The FBI Code Cracking Challenge

The FBI embedded the above code as a flash file. The code for all you cryptanalysts
VFWTDLCSWV. YD NSLMIJFWEJFD GSW SL NIJNQBLM FOBV EJFDVF DLNIGTFBSL.KBVBF YYY.AHB.MSK/NSCDC.OFZ FS EDF WV QLSY SA GSWI VWNNDVV.
More resources to solve this challenge
2008 FBI Code Cracking Challenge: http://www.fbi.gov/page2/dec08/code_122908.html
2007 FBI Code Cracking Challenge: http://www.fbi.gov/page2/nov07/code112107.html
Analysis of Criminal Codes and Ciphers: http://www.fbi.gov/hq/lab/fsc/backissu/jan2000/olson.htm
Spoiler Alert: How to solve the 2008 FBI Crypto challenge
** try to solve this before scrolling down **
Solving FBI 2008 Crypto Challenge
1. An easy giveaway was the 5th line from the crypto picture embedded above
YYY.AHB.MSK/NSCDC.OFZ
substituting www for yyy. Another hint it is likely they were pointing to fbi.gov. So far we have
Y – W
A – F
H – B
B – I
M – G
S – O
K – V
2. Substituting in the word before that URL. For KBVBF, we can deduct it is VISIT
3. Next word to guess is FOBV in the 3rd line. Substituting we can deduct is is THIS
4. Next word is YD on the first line. The only alphabet that made sense there is E. So we have D – E
5. Next, I would try to start solving any 2, 3, 4 alphabet groupings.
Following is a screenshot of my whiteboard. The numbers on the left to each word represented the order in which i tackled the words
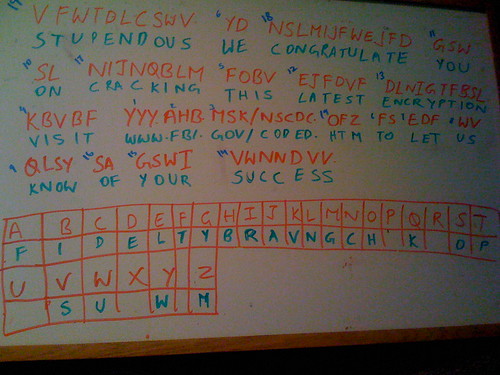
Once you solve and substitute the cipher comes out as
Stupendous. We congratulate you on cracking this latest encryption. Visit www.fbi.gov/coded.htm to let us know of your success.
Visiting the URL above gives us this
Congratulations, you did it! Thanks for participating, and happy holidays.

Hi Ajit,
As we can see this is simple substitution cipher but like last time it also seems to be a secret keyword substitution cipher.
S E C R T L Y A B D F G H I J K M N O P Q U V W X Z
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
Last times solution
secret word was “FEDERAL BUREAU OF INVESTIGATION”
i.e the plain text “FEDRALBUOINVSTGCHJKMPQWXYZ”
would result in cipher alphabet “ABCDEFGHIJKLMNOPQRSTUVWXYZ”
This time seems to be matching “FIDELITY BRAVING”
i.e. the plain text “FIDELTYBRAVNGCHJKMOPQSUWXZ”
would result in cipher aplphabet “ABCDEFGHIJKLMNOPQRSTUVWXYZ”
But it gets two letters wrong i.e we know cipher Y is plain W and cipher Z is M. going by YYY is WWW and OFZ is HTM
so by introducing cycling this by two letters to get this right
i.e. the plain text “WMFIDELTYBRAVNGCHJKOPQSUXZ”
would result in cipher aplphabet “YZABCDEFGHIJKLMNOPQRSTUVWX”
this gives the desired solution but not as elegant “WM FIDELITY BRAVING” with a cyclic shift of 2 letters does not seem to be such an elegant secret
Any thoughts??
I noticed cipher R is still a problem 🙁
If the FBI can really use codes this complex…how come we still haven’t got binLaden?
If the FBI can really use codes this complex…how come we still haven’t got binLaden?
This is actually a variant of the most common type encryption in the world. The daily cryptoquip in your newspaper uses the same exact type of encryption.
Took me like 2 minutes with Notepad and “match case” replacements. 😀
I think you just missed a HUGE chunk of sarcasm flying your way there Mike.
under totally seems serious, poor sarcasm
No, pretty obvious he was being sarcastic, poor understanding
Encryption has long been used by militaries and governments to facilitate secret communication. Encryption is now commonly used in protecting information within many kinds of civilian systems. For example, in 2007 the U.S. government reported that 71% of companies surveyed utilized encryption for some of their data in transit. Encryption can be used to protect data “at rest”, such as files on computers and storage devices (e.g. USB flash drives). In recent years there have been numerous reports of confidential data such as customers’ personal records being exposed through loss or theft of laptops or backup drives. Encrypting such files at rest helps protect them should physical security measures fail. Digital rights management systems which prevent unauthorized use or reproduction of copyrighted material and protect software against reverse engineering (see also copy protection) are another somewhat different example of using encryption on data at rest.
Encryption is also used to protect data in transit, for example data being transferred via networks (e.g. the Internet, e-commerce), mobile telephones, wireless microphones, wireless intercom systems, Bluetooth devices and bank automatic teller machines. There have been numerous reports of data in transit being intercepted in recent years.[2] Encrypting data in transit also helps to secure it as it is often difficult to physically secure all access to networks.
Encryption, by itself, can protect the confidentiality of messages, but other techniques are still needed to protect the integrity and authenticity of a message; for example, verification of a message authentication code (MAC) or a digital signature. Standards and cryptographic software and hardware to perform encryption are widely available, but successfully using encryption to ensure security may be a challenging problem. A single slip-up in system design or execution can allow successful attacks. Sometimes an adversary can obtain unencrypted information without directly undoing the encryption. See, e.g., traffic analysis, TEMPEST, or Trojan horse.
One of the earliest public key encryption applications was called Pretty Good Privacy (PGP), according to Paul Rubens. It was written in 1991 by Phil Zimmermann and was purchased by Network Associates (now PGP Corporation) in 1997.
The best types of encryption are duel layer and combinations of ciphers whereby the information as well as the system space it’s stored in is encrypted beyond recovery. With encryption algorithms that possess incredible amounts of strength these days, I find it highly amusing they still resort to the ceaser cipher, when there are far better method’s for low level encryption.
What self respecting crypto expert would try to secure something with a plain shift? Thats so 80’s cold war and spooks in the arms race!